Comment sections across social platforms have quietly evolved into high-yield hunting grounds for scammers. What once were simple reactions, quick questions, or casual exchanges now function as entry points into elaborate criminal funnels. The scammers behind these comments operate under a variety of guises, and each form has a distinct motive.
ROMANCE AND AFFECTION LURES

Romance-style comments are among the most emotionally manipulative. These typically appear as flattering remarks such as “I love what you post, please message me privately,” or similar wording that seems personal even though it does not reference anything specific from the original post. The goal is to move the target into private conversation where the scammer can begin grooming, request sensitive information, introduce emotional dependency, or eventually send links to malicious pages. Many of these accounts use stolen photos from legitimate people or AI-generated likenesses designed to appear approachable, single, and trustworthy.
CATFISHING PROFILES AND SOCKPUPPETS
Closely related are catfishing profiles. These accounts are developed to look believable by posting copied content, adding staged friends, and leaving comments on multiple unrelated posts to simulate authenticity. Once a target responds, the scammer can escalate toward emotional fraud, emergency financial requests, or attempts to gather personal data such as address details, phone numbers, banking information, or images that can later be weaponized in extortion attempts. Romance-based scams often run for weeks, months and even years because the profit per victim can be high and emotional leverage strong.
FAKE VIDEO LINKS AND CLICKBAIT
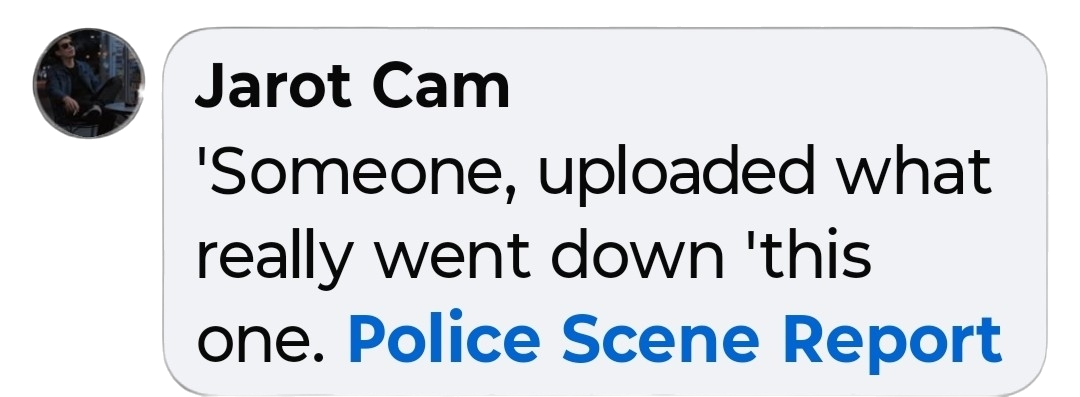
Another prominent strain of comment scams are fake video links. These usually carry sensational language promising shocking footage, celebrity scandals, crime recordings, or exclusive clips. Clicking these links typically leads to a fake login page disguised as a familiar platform sign-in screen. Victims believe they are being asked to verify credentials, but instead, their passwords are harvested in real time. Those credentials are sold, used to breach other services where passwords are reused, or used to hijack accounts and spread similar scams through the victim’s friend network.
CREDENTIAL PHISHING AND MALWARE DELIVERY
Alongside credential harvesting, some pages redirect victims to forced download prompts disguised as video players or “missing codecs,” a common disguise for malware installers. Users who click through these prompts may end up with remote access trojans, information stealers, or ransomware quietly installed in the background. Malware installation is particularly lucrative because it allows scammers to recruit devices into botnets or extract sensitive data silently.
AFFILIATE AND AD FRAUD
Some comment scams are less technical but still profitable. Affiliate traps and ad fraud aim to push users through pages packed with sponsored ads, fake giveaways, misleading subscription forms, and “free trial” offers eventually turning into recurring charges. These accounts are often staged to simulate engagement, which makes future malicious links appear more credible. Social proof and engagement farming are key strategies to amplify scams across platforms.
MOTIVES BEHIND THE SCAMS
Scammers operate for multiple reasons. Some seek direct financial gain through money transfers or gift cards. Others collect credentials for resale or identity theft. Malware campaigns recruit devices for botnets used in spam, attacks, or crypto mining. Affiliate revenue, ad monetization, and behavioral tracking are also common. Across all these motives, the trigger remains a small comment engineered to provoke curiosity, affection, or urgency.
SPOTTING SUSPICIOUS COMMENTS
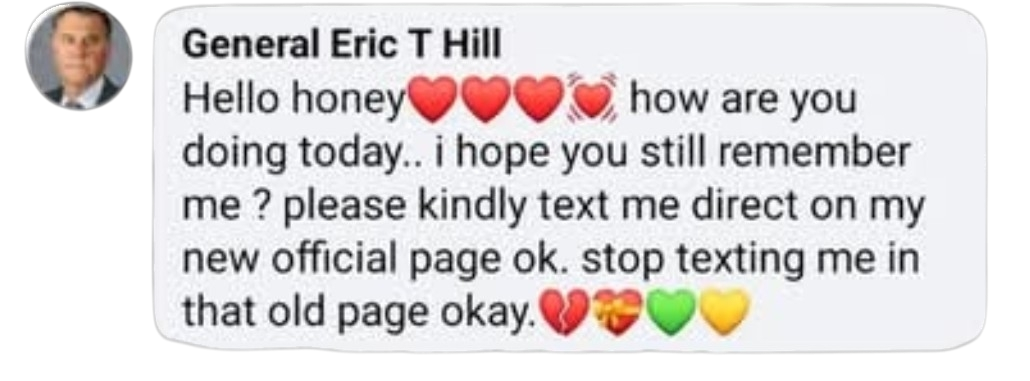
Suspicious comments often contain generic praise, broken sentence structures, or language pressuring the reader to act immediately. Any comment attempting to shift communication into private channels should be treated with caution. Links requiring login to view a video, particularly when you are already logged in, are red flags. Profiles with generic stock-style photos, little original content, or commenting-only activity are also suspect.
Here is a clean add on section you can drop directly into the article. It mirrors the tone of the example comment and explains the tactic clearly without mentioning love bombing or hyperlinks.
BENIGN LOOKING ENGAGEMENT REQUESTS
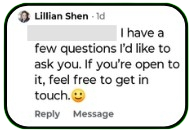 Not all comment based scams begin with obvious flattery, urgency, or links. Some are deliberately understated and appear completely normal at first glance. A common variation involves a simple, polite request framed as curiosity or interest, such as asking to speak privately or requesting clarification about a comment.
Not all comment based scams begin with obvious flattery, urgency, or links. Some are deliberately understated and appear completely normal at first glance. A common variation involves a simple, polite request framed as curiosity or interest, such as asking to speak privately or requesting clarification about a comment.
These messages often read as reasonable and non threatening, for example requesting to ask a few questions and inviting the person to get in touch if they are open to it. Because there is no link, no sales pitch, and no emotional manipulation on display, the comment blends naturally into legitimate discussion.
This approach has a specific advantage for scammers. By prompting the target to initiate the private message themselves, the interaction bypasses many platform messaging and spam detection systems. The platform sees the conversation as user initiated rather than unsolicited outreach, reducing the likelihood of automated warnings or restrictions.
Once the conversation moves to private messages, the scammer can gradually introduce the real objective, whether extracting information, building false credibility, or steering the target toward a later romance, financial or social engineering scheme. The initial comment serves only as a low risk door opener, not the scam itself.
Because these comments appear harmless, they are often overlooked by moderators and ignored by readers as a non issue, making them one of the more effective and difficult to detect comment based scam tactics.
WHAT TO DO IF YOU ENCOUNTER A SCAM
If a suspicious link has been clicked, close the browser immediately, clear cookies, and run a malware scan. If credentials were entered, change passwords from a clean device and activate multi-factor authentication. Compromised accounts should be force logged out of all sessions, and financial institutions alerted if banking data was exposed. Reporting the attempt to the platform and warning others reduces the attacker’s reach.
Comment scammers depend on speed and volume. They post widely, often using automated systems, expecting only a small percentage of people to respond. While comments appear harmless, what follows can range from identity theft to financial loss, long-term harassment, or compromised devices used in further cybercrime. Awareness, public reporting, and cautious engagement are the strongest defenses. A single flattering line or shocking video teaser is rarely casual, it is often bait laid for whoever clicks first.
- Log in to post comments
