EYE IN THE SKY: How Predatory Contractors Use Drones to Manufacture Damage
It often begins with an unexpected knock at the door. A salesperson is standing there, offering home improvement services, and you respond the way most sensible homeowners do when faced with an unsolicited cold call by politely declining.
What follows has been reported by many homeowners as extremely unsettling. Instead of leaving, the salesperson pulls out a tablet or phone and explains
I understand your hesitation, you should see the images first.

 For most people, a bucket list represents a lifetime of aspirations. Witnessing a historic sporting event, attending a sold out concert, or finally taking that once imagined luxury safari. International fraud syndicates have found a way to weaponize those dreams.
For most people, a bucket list represents a lifetime of aspirations. Witnessing a historic sporting event, attending a sold out concert, or finally taking that once imagined luxury safari. International fraud syndicates have found a way to weaponize those dreams.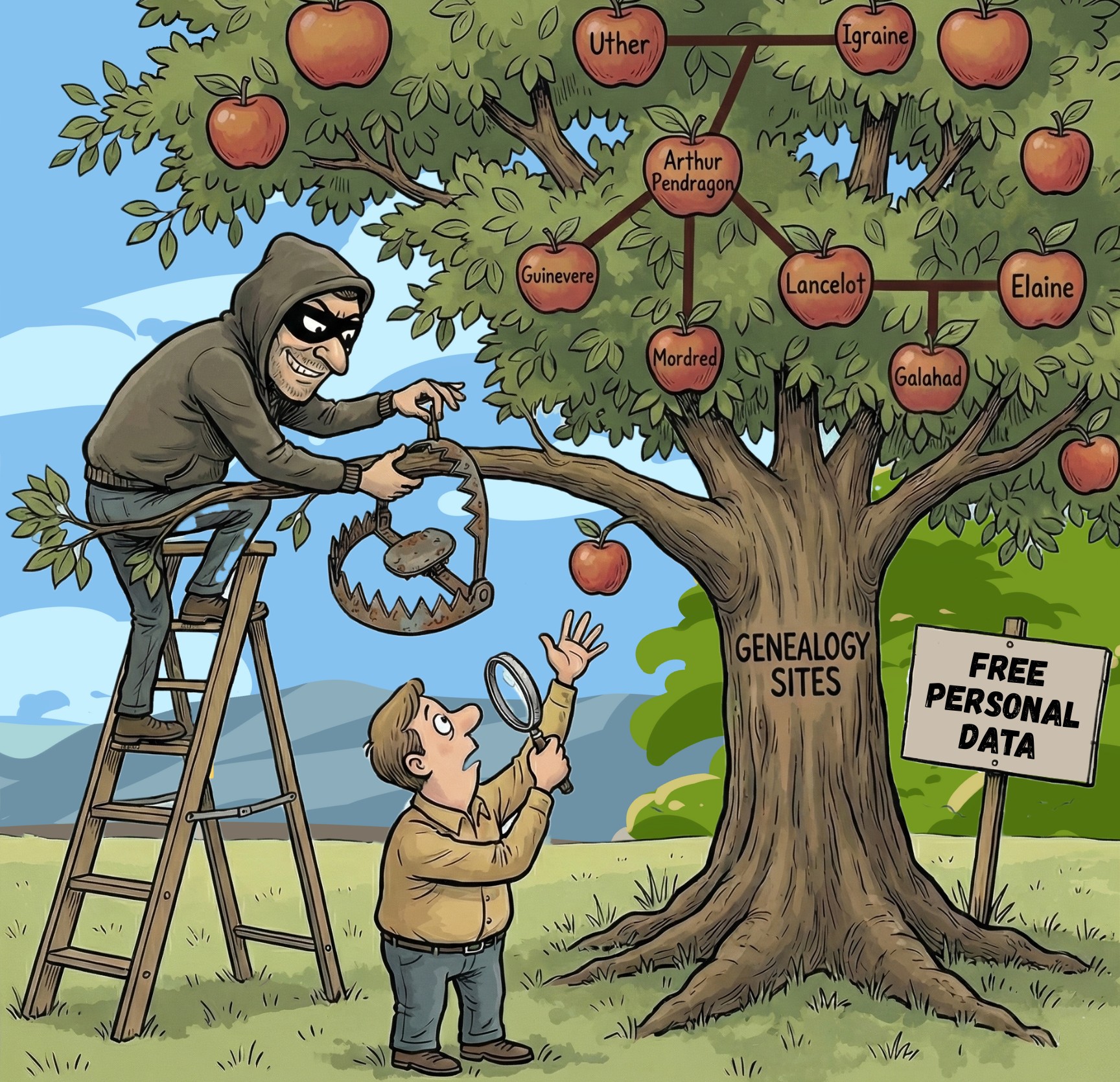 For millions of people worldwide, submitting a DNA sample or building an online family tree is an act of trust; it is about identity, belonging, and reconnecting with lost history. Genealogy platforms have turned this deeply personal pursuit into massive digital ecosystems built on shared information and emotional connection.
For millions of people worldwide, submitting a DNA sample or building an online family tree is an act of trust; it is about identity, belonging, and reconnecting with lost history. Genealogy platforms have turned this deeply personal pursuit into massive digital ecosystems built on shared information and emotional connection. For years, consumers have been trained to distrust emails and text messages; people scan for typos, suspicious sender addresses, and generic greetings before clicking anything.
For years, consumers have been trained to distrust emails and text messages; people scan for typos, suspicious sender addresses, and generic greetings before clicking anything. 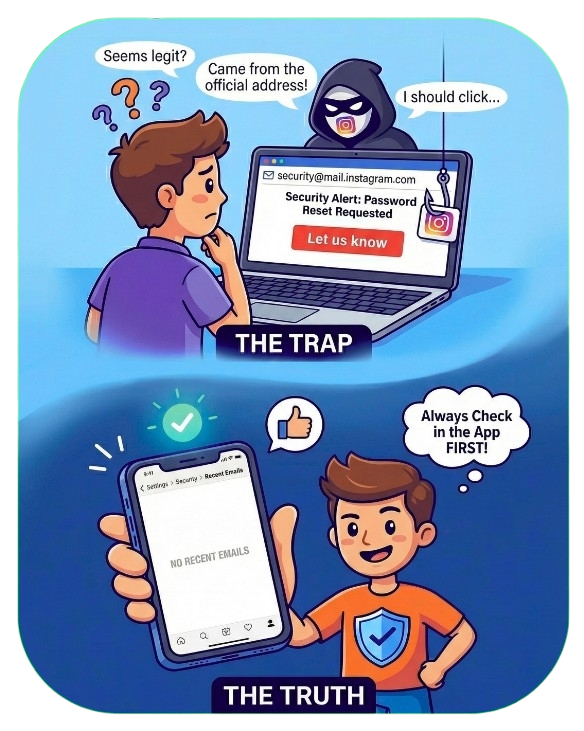 A large scale phishing operation is actively targeting Instagram users worldwide using fake security alert emails appearing to come from a legitimate Instagram Notification Email Address. The messages claim a password reset was requested and prompt users to click a “Let us know” link if the activity was not authorized.
A large scale phishing operation is actively targeting Instagram users worldwide using fake security alert emails appearing to come from a legitimate Instagram Notification Email Address. The messages claim a password reset was requested and prompt users to click a “Let us know” link if the activity was not authorized. There has been a recent sustained surge in highly organized email attacks targeting Microsoft account holders worldwide.
There has been a recent sustained surge in highly organized email attacks targeting Microsoft account holders worldwide. The digital backbone of global diplomacy and international research is now facing a more refined and dangerous cyber threat. State sponsored actors are no longer relying on obvious malware or crude phishing. According to a recent FBI warning, North Korea linked cyber units have significantly evolved their methods to quietly bypass modern security defenses.
The digital backbone of global diplomacy and international research is now facing a more refined and dangerous cyber threat. State sponsored actors are no longer relying on obvious malware or crude phishing. According to a recent FBI warning, North Korea linked cyber units have significantly evolved their methods to quietly bypass modern security defenses. Scammers are finding a new way to leverage artificial intelligence in their operations. Previously, I wrote an article on
Scammers are finding a new way to leverage artificial intelligence in their operations. Previously, I wrote an article on